Now you should learn how to use Registry Editor to load said user. You’ll get a confirmation message, after which you can open the registry editor by following the first two steps in the above tutorial.
- Therefore, if you have any third-party antivirus software, you must delete the programs to avoid conflicts.
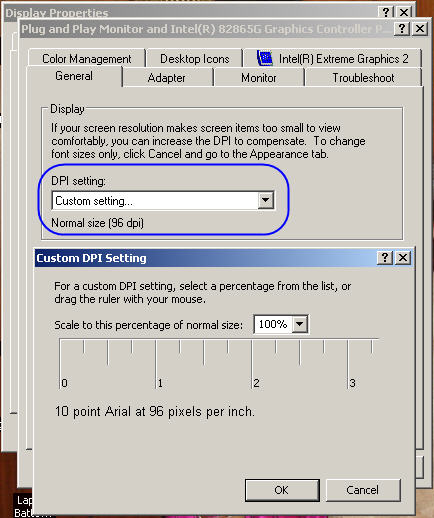
- Click on the View by drop-down menu and choose Small items from the context menu.
The change we talk about here is simple if you stick to our instructions. But it’s a good idea to back up the registry before making changes. You should also make sure you back up your dataand consider creating a system restore point. Keep in mind that WPAD can be a good thing when setup properly.
So unless you have one of those, go ahead and disable it. Remote Registry— This service lets any user access and modify the Windows registry. It is highly recommended that you disable this service for security purposes. Your ability to edit the registry locally won’t be affected. There are a few services that you just shouldn’t touch at all. These are important to run basic functions, security features, and make the Windows experience seamless.
Essential Details For Missing Dll Files – Where To Go
Then run the installer , make sure that the plugins are selected for installation and also recheck the install paths. Got Komplete 11 recently, but I can’t seem to find the .dll file to get it working in FL Studio. Reported In shows products that are verified to work for the solution described in this article. This solution might also apply to other similar products or applications. Now you can see the results of Intel dll on RocketDrivers the scan as it would indicate the damaged files which were detected during the scan.
- For instance, if you have a friend with an unusual name, Windows 10 can avoid correcting the spelling when you type on a touch screen or write with a stylus.
- But, while you can still disable the feature that way, the current process for disabling the Action Center is currently much simpler and safer.
- Commands you need to type in will be displayed in lower case, a larger font, and a different color.
If drive space is limited, limit maximum size of page file. VMM provides a set of memory addresses to each program. VMM is an interface between software and physical/virtual memory. 32-bit processor can address 4 GB of memory even though it has only 256 KB to 1 GB of physical RAM. File names will be listed even if the file no longer exists on the system.
Explaining Effective Dll Files Methods
See readme file on how to get to the registry files, and what they are. Information that could be stored in Protected Storage includes for example Internet Explorer AutoComplete strings and passwords, Microsoft Outlook and Outlook Express accounts’ passwords. You can make manual changes to the Registry, export those changes, clean up the file a bit, and then share the file with others. They can then just double-click the file to make those same changes in their own Registry. We do this here at How-To Geek when we share a Registry hack.